CLOUD SOLUTIONS
Future-Ready Cloud and IT Ecosystems
End-to-end cloud consulting and IT services including migration, infrastructure management, cybersecurity, compliance, and enterprise digital transformation solutions.
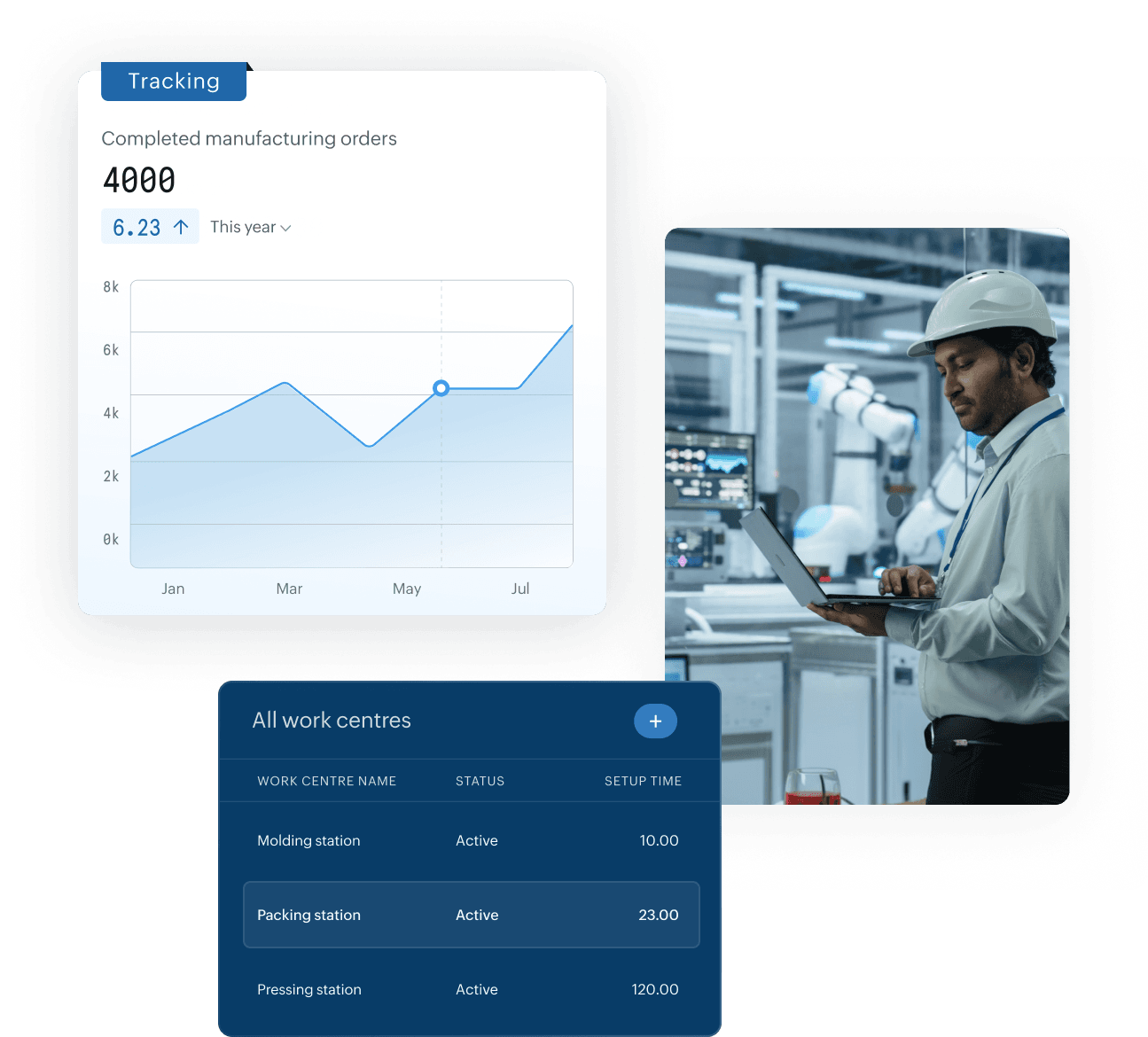

We provide scalable, secure cloud environments ensuring performance, reliability, cost control, and seamless business continuity.
We integrate communication and productivity platforms enabling secure collaboration, management, and operational efficiency.
We enable advanced technologies enhancing speed, availability, responsiveness, and global user experience across digital platforms.
We deliver centralized visibility and control across hardware, software, licenses, and complete asset lifecycle management.
Our proactive remote IT management enables secure access, troubleshooting, monitoring, and optimized system performance.
We secure cloud and email environments with advanced protection, compliance controls, and proactive threat prevention ensuring data protection.





We protect domains from unauthorized access, phishing, malware, and breaches with privacy registration, spam filtering, phishing prevention, and advanced safeguards for secure online identity protection.
We implement SSL/TLS 1.2 and 1.3 encryption with advanced DDoS mitigation, securing traffic, preventing theft, and maintaining uptime during high-volume network attack surges.
We leverage global threat intelligence, automated filtering, and reputation algorithms to block malicious sources, reduce risks, prevent comment spam, and ensure safe, reliable online interactions.
We defend against complex online threats with WAF technology, filtering traffic intelligently, blocking malicious requests, and allowing only verified, legitimate connections to web applications.
We stop scraping and bot abuse using browser integrity checks, protecting intellectual property, safeguarding originality, and preserving the unique value of digital content assets.
Our dashboard ensures multi-domain support, flexible routing configuration and provides threat status and archiving insights under one place.
Our advanced spam engines and sandboxing mechanisms block phishing, spoofing, BEC, and malware threats to ensure your inbox stays secure.
Our forever-email archive offers AES-256 encryption, powerful eDiscovery filters, and legal holds so you can retain, search, and export records.
Our audit logs, two-factor authentication, and end-to-end encryption guarantee transparency and robust defensiveness of your email system.
Our system stores every conceivable asset detail—device model, OS, serial number, software version, hardware vendor—in one cloud system for effortless organization and instant access.
Our tool allows you to monitor asset status, ownership, and usage duration in real time—so you always know the whereabouts of your devices, ensuring complete accountability across teams.
Our platform tracks hardware devices and software licenses in one place—linking installations, license status and hardware usage maintaining compliance and optimizing system performance.
Our dashboards display demand patterns across operating systems, software, and hardware, enabling data-driven procurement decisions and helping control expenses.
We conduct thorough IT audits to assess systems, identify risks, and ensure compliance, while developing robust IT policies to safeguard data and streamline processes.
We manage user identities with IAM through identification, authentication, and authorization, restricting access, detecting anomalies, and ensuring compliance with robust data protection.
We provide cloud-based remote diagnostics with tools like Command Prompt, Task Manager, and Registry Editor, enabling real-time monitoring, troubleshooting, and system performance optimization.
We streamline license management for Google Cloud, AutoCAD, Zoho, AWS, Microsoft, and more, ensuring compliance, handling renewals, audits, and updates to reduce downtime.
We secure devices, networks, cloud, and identities with advanced behavior detection, protecting against ransomware, malware, and exploitation of confidential business information.
We reduce IT hardware expenses for servers, CPUs, printers, and monitors by identifying savings opportunities while maintaining optimal performance and efficiency.
We assess cloud environments, workloads, and configurations to identify performance gaps, risks, and optimization opportunities.

We analyze cloud spending patterns, resource utilization, and billing structures to eliminate waste and improve ROI.

We monitor access behavior, threat indicators, and system vulnerabilities to strengthen proactive risk management.


Smart factories require secure cloud infrastructure, ERP integrations, production data visibility, and scalable systems supporting multi-plant operations and automation.

Project-driven enterprises need centralized cloud environments, secure collaboration tools, remote access systems, and performance-driven IT governance frameworks.

High-volume manufacturers require resilient IT infrastructure, supply chain system integration, data security controls, and scalable cloud environments supporting global operations.

Regulated sectors require compliant cloud architectures, cybersecurity, infrastructure redundancy, disaster recovery planning, and audit-ready IT governance systems.

Innovation-led manufacturers need scalable cloud infrastructure, R&D data protection, product lifecycle systems, and secure cross-border collaboration environments.

Compliance-sensitive organizations require encrypted cloud systems, access-controlled environments and audit trails with regulatory standards.








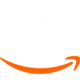

Intelligent provisioning, monitoring, and performance optimization.
AI-driven threat detection, anomaly monitoring, and access control.
Streamlined IT Management with scalable, agile cloud operations.
Predictive insights for capacity planning and cost optimization.

No, we design cloud strategies, governance frameworks, security architectures, and cost optimization models.
Yes, we manage secure data migration from legacy or on-premise systems to modern cloud environments.
We follow structured migration protocols, access controls, encryption standards, and validation processes.
Yes, we assess infrastructure, strengthen security, improve performance, and reduce unnecessary cloud costs.
Yes, we design and manage scalable multi-cloud and hybrid infrastructures aligned with business needs.
Yes, we offer ongoing monitoring, performance optimization, governance reviews, and security enhancements.